Drones had become extremely popular between enthusiasts of aerial filming and photography. But what if they venture into the areas where their presence is unwanted? In this video, my last within Kaspersky, we focus on the solution for this problem — in a civilized way.
Do businesses have to play games?
It seems like everyone is talking about gamification. But is it really applicable to every sphere of business? The topic of this live stream was how to use gamification in education in general, and information security in particular.
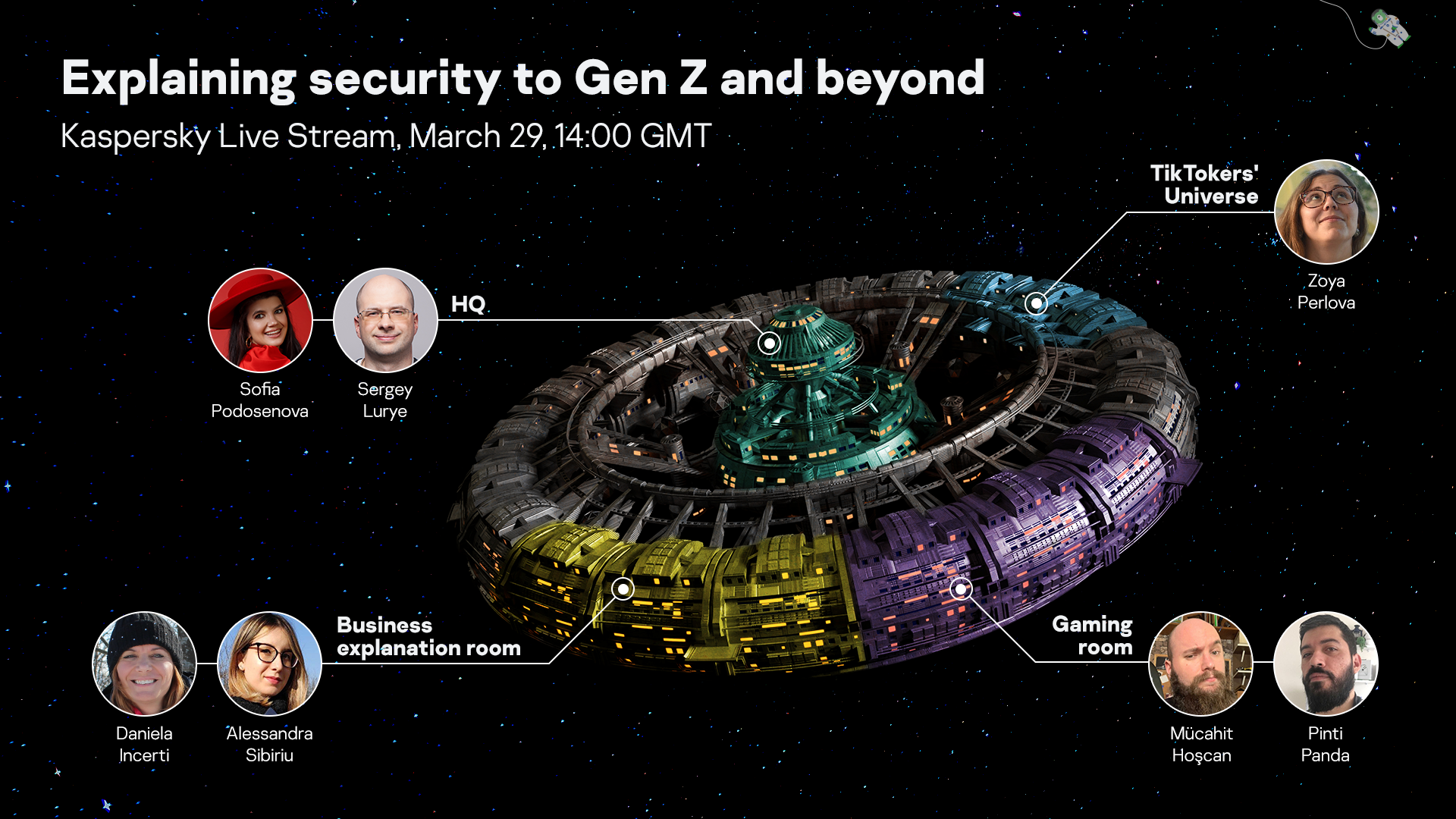
How to explain security to Gen Z and beyond?
It may seem that we are generations and interests apart, and drift away with accelerating speed, just like Galaxies in the University.
How can businesses explain abstract concepts like information security to different target audiences? How can we get the influencers on board and what effect we can actually achieve?
The future of work? Own it!
How will the future post-COVID19 world look like? What will the work-life balance be in the new normal?
We have invited our colleagues from Japan, Singapore, UAE, Italy, France, Germany, UK, Spain, USA, Colombia, and Brazil, to share their views and thoughts on the interactive video adventure at kas.pr/oyf.
How to succeed in negotiating with partners in Southeast Asia?
In a nutshell, it boils down to a principle: «talk less, listen more». This was the main conclusion we have arrived to during a talk with Shan Loy, Shan Loy, Academic Partnerships Manager, Kaspersky APAC.
Watch the video to learn more:
What’s more important: skills or knowledge?
In the classic scheme of thought, the hierarchy of training the neural network hosted between the human’s ears is as follows: first, you gain knowledge, then you apply this knowledge to solve some real (or synthetic, if you’re in academia) tasks, and after a while, you gain habits.
But modern workplace mostly worries about the skills and doesn’t really care about the knowledge. Watch our debate with Evgeniya Russkikh, Senior Educational Programs Manager, Kaspersky, on the importance of skills vs. the importance of knowledge in today’s fast-paced world.
How did the COVID19 pandemic affect online education?
In September, 2020, we took a look at how the COVID19 pandemic affected the global online education segment together with our Head of Global Research and Analysis Team (GReAT) in EMEA, Maria Namestnikova:
Experiment: How easy is it to spy on a smartwatch wearer?
Can a smartwatch be used to spy on its owner? Sure, and we already know lots of ways. But here’s another: A spying app installed on a smartphone can send data from the built-in motion sensors (namely, accelerometer and gyroscope) to a remote server, and that data can be used to piece together the wearer’s actions — walking, sitting, typing, and so on.
A reprint from the original publication on Kaspersky Daily blog from May 30, 2018.
How extensive is the threat in practice, and what data can really be siphoned off? We decided to investigate.
Experiment: Can smartwatch movements reveal a password?
We started with an Android-based smartwatch, wrote a no-frills app to process and transmit accelerometer data, and analyzed what we could get from this data. For more details, see our full report.
The data can indeed be used to work out if the wearer is walking or sitting. Moreover, it’s possible to dig deeper and figure out if the person is out for a stroll or changing subway trains — the accelerometer patterns differ slightly; that’s also how fitness trackers differentiate between, say, walking and cycling.
It’s also easy to see when a person is typing on a computer. But working out what they are typing is way more complex. Everyone has a specific way of typing: the ten-finger method, the one- or two-digit keyboard stab, or something in-between. Basically, different people typing the same phrase can produce very different accelerometer signals — although one person entering a password several times in a row will produce pretty similar graphs.
So, a neural network trained to recognize how a particular individual enters text could make out what that person types. And if this neural network happens to be schooled in your particular way of typing, the accelerometer data from the smartwatch on your wrist could be used to recognize a password based on your hand movements.
However, the training process would require the neural network to track you for quite a long time. The processors in modern portable gadgets are not powerful enough to run a neural network directly, so the data has to be sent to a server.
And therein lies trouble for a would-be spy: The constant upload of accelerometer readings consumes a fair bit of Internet traffic and zaps the smartwatch battery in a matter of hours (six, to be precise, in our case). Both of those telltale signs are easy to spot, alerting the wearer that something is wrong. Both, however, are easily minimized by scooping up data selectively, for example when the target arrives at work, a likely time for password entry.
In short, your smartwatch can be used to identify what you’re typing. But it’s hard, and accurate recovery relies on repeat text entry. In our experiment, we were able to recover a computer password with 96% accuracy and a PIN code entered at an ATM with 87% accuracy.
It could be worse
For cybercriminals, however, such data is not all that useful. To use it, they’d still need access to your computer or credit card. The task of determining a card number or CVC code is way trickier.
Here’s why. On returning to the workplace, first thing the smartwatch owner types is almost certainly a password to unlock their computer. That is, the accelerometer graph indicates first walking, then typing. Based on data obtained just for this brief period, it’s possible to recover the password.
But the person won’t enter a credit card number as soon as they sit down — or get up and walk away immediately after entering that data. What’s more, no one will ever enter this information several times in short succession.
To steal data-entry information from a smartwatch, attackers need predictable activity followed by data entered several times. The latter part, incidentally, is yet another reason not to use the same password for different services.
Who should worry about smartwatches?
Our research has shown that data obtained from a smartwatch acceleration sensor can be used to recover information about the wearer: movements, habits, some typed information (for example, a laptop password).
Infecting a smartwatch with data-siphoning malware that lets cybercriminals recover this information is quite straightforward. They just need to create an app (say, a trendy clockface or fitness tracker), add a function to read accelerometer data, and upload it to Google Play. In theory, such an app will pass the malware screening, since there is nothing outwardly malicious in what it does.
Should you worry about being spied on by someone using this technique? Only if that someone has a strong motivation to spy on you, specifically. The average cybercrook is after easy pickings and won’t have much to gain.
But if your computer password or route to the office is of value to someone, a smartwatch is a viable tracking tool. In this case, our advice is:
- Take note if your smartwatch is overly traffic-hungry or the battery drains quickly.
- Don’t give apps too many permissions. In particular, watch out for apps that want to retrieve account info and geographical coordinates. Without this data, intruders will struggle to ascertain that it’s your smartwatch they’ve infected.
- Install a security solution on your smartphone that can help detect spyware before it starts spying.